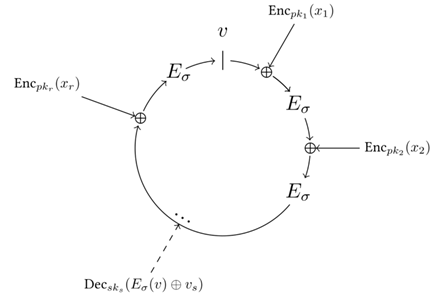
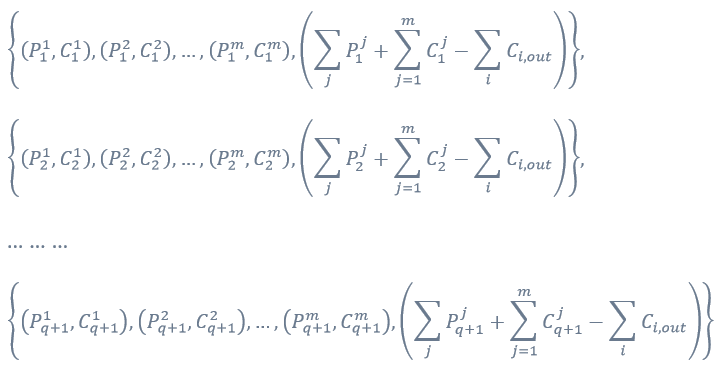The QURAS Blockchain implemented the anonymization of the transaction by realizing the encryption of the transaction contents.
The basic problem of anonymizing transactions is how to verify the contents of the encrypted transaction from the Consensus Node.
That is, the Consensus Node must be able to prove that the encrypted transactions are accurate without the use of decryption keys for encrypted transactions.
In order to implement this, the Zero-Knowledge Proof, a zero-knowledge encryption algorithm, can be used to verify the accuracy of encrypted transactions even without a real decryption key (private key) on the Consensus Node.
The ZK - SNARKS is a module that implements this ZKP.
Let's start by looking at the concept of Zero-Knowledge Proof.